Penetration Testing
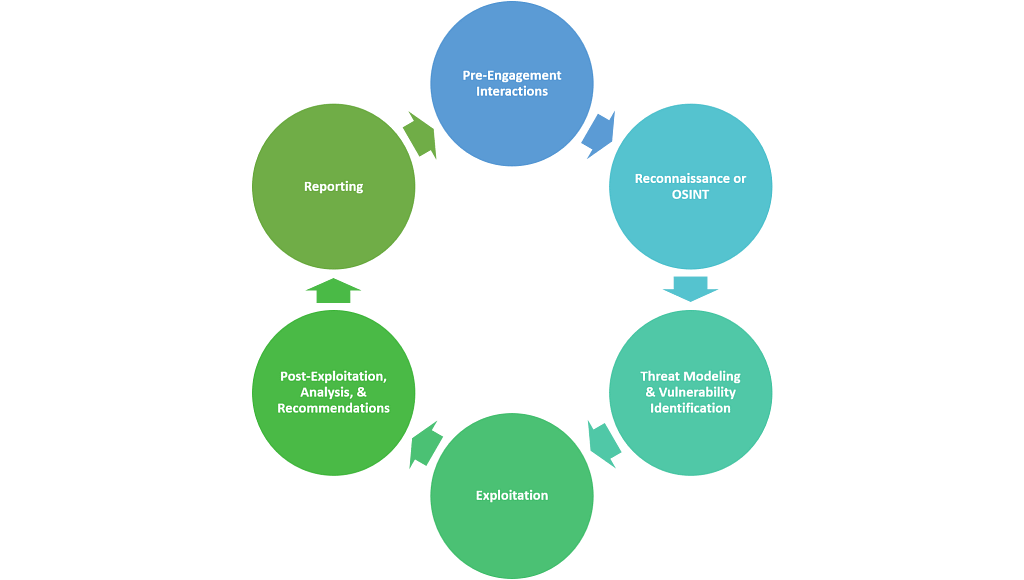
In security, like in life, identifying your own weaknesses can be challenging. Thankfully, IPRS Consultants excels at thoroughly documenting vulnerabilities. Understanding your flaws and potential avenues of exploitation by attackers is crucial for enhancing your security program. With this in mind, our Penetration Testing Services team conducts real-world attack simulations on your networks, applications, devices, and personnel. This process reveals the security status of your critical systems and infrastructure and provides insights into strengthening them. Just like a caring parent, we highlight your shortcomings not to upset you, but because we genuinely care about your security.